If you manage an enterprise network with at least one guest network, you need a system that provides centralized management of all your access points as well as separates the guest network from internal network with security measures against the infilteration of sensitive company documents by unauthorized users. For such environment, we will set up the Mikrotik capsman with vlan and dual ssid to provide wireless coverage for company staff and guest without compromising the security of our internal network.
Dual ssids will be dynamically configured on all access points with each ssid assigned to a vlan. On the capsman, we will configure a firewall filter rule to restrict the guest vlan access to the internal network.
Configure Mikrotik capsman with vlan and two SSIDs
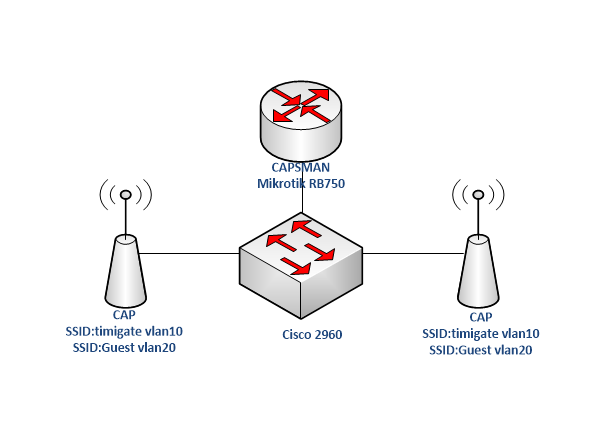
On the Mikrotik RB750 that serves as my capsman, I will create two vlans: vlan10 and vlan20. The vlans will be attached to ether2 which is my trunk connection to my a Cisco Catalyst 2960 switch. I will also configure two dhcp servers for the two vlans. See commands below.
Create vlans on the capsman
/interface vlan add interface=ether2 name=VLAN10 vlan-id=10 add interface=ether2 name=VLAN20 vlan-id=20 /ip address add address=192.168.10.1/24 interface=VLAN10 add address=192.168.20.1/24 interface=VLAN20 /ip pool add name=dhcp_pool10 ranges=192.168.10.2-192.168.10.254 add name=dhcp_pool20 ranges=192.168.20.2-192.168.20.254 /ip dhcp-server add address-pool=dhcp_pool10 disabled=no interface=VLAN10 name=dhcp10 add address-pool=dhcp_pool20 disabled=no interface=VLAN20 name=dhcp20 /ip dhcp-server network add address=192.168.10.0/24 dns-server=8.8.8.8 gateway=192.168.10.1 add address=192.168.20.0/24 dns-server=8.8.8.8 gateway=192.168.20.1
Configure capsman with two SSIDs for the two vlans
/caps-man configuration
add country=Nigeria datapath.local-forwarding=yes datapath.vlan-id=10 datapath.vlan-mode=use-tag name=Timigate security.authentication-types=wpa-psk,wpa2-psk \
security.passphrase=TimiGate1234 ssid=Timigate
add country=Nigeria datapath.local-forwarding=yes datapath.vlan-id=20 datapath.vlan-mode=use-tag name=Guest security.authentication-types=\
wpa-psk,wpa2-psk security.passphrase=Guest1234 ssid=GUEST
Also read: RouterOS update changes how to configure Mikrotik IPSEC L2TP VPN
Provisioning rule on the capsman
We will create a single provioning rule on the capsman for the two vlans. This rule will create the two SSIDs (Timigate and Guest on all connected access points, also known as Caps). See Commands below.
/caps-man provisioning add action=create-dynamic-enabled master-configuration=Timigate slave-configurations=Guest
Enable Capsman manager and limit capsman to a single interface (ether2)
/caps-man manager interface set [ find default=yes ] forbid=yes add disabled=no interface=ether2 set enabled=yes
Read: How to configure Mikrotik GRE Tunnel for Site to Site VPN using IPSEC for encryption
Secure internal network from guest
On the RB750, configure a firewall filter rule to drop all packets coming from the Guest vlan to Vlan10. See commands below.
/ip firewall filter add chain=forward src-address=192.168.20.0/24 dst-address=192.168.10.0/24 action drop
Configure vlan on Cisco Catalyst 2960 switch
On the 2960 switch, the port connecting to the Mikrotik RB750 router and those connecting to the Mikrotik access points (caps) will be configured as a trunk ports while the rest will be access ports. Vlans 10 and 20 will be allowed through the trunk ports. See commands below:
Switch>en Switch#conf t Switch(config)#vlan 10 Switch(config-vlan)#name Timigate Switch(config-vlan)#vlan 20 Switch(config-vlan)#name Guest Switch(config-vlan)#int ran f0/1 -3 Switch(config-if-range)#sw mode trunk Switch(config-if-range)#sw trunk allowed vlan 10,20 Switch(config-if-range)#int ran f0/4 -24 Switch(config-if-range)#sw mode access
Connect access points to trunk ports on the Cisco router and you are good to go!
If you enjoyed this tutorial, please subscribe to this blog to receive my posts via email. Also subscibe to my YouTube channel, like my Facebook page and follow me on Twitter.

So many thanks for shating this, I have a question, I have a cisco MLS which does inter vlan routing between some access switch and capsman and their caps are plugged to access switches, so I don’t need to create interface vlan on capsman because MLS handles that,furthemore I don’t need to config dhcp on capsman because I have a microsoft dhcp server on network,however after configuration I cannot see guest ssid. Can you please help me?